OpenClaw Setup: Why Your Omnichannel Agent Keeps Falling Out of Sync
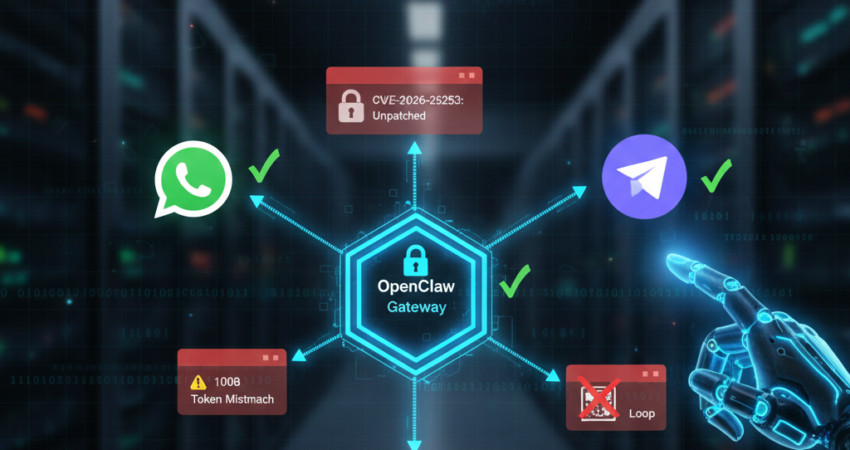
Openclaw setup errors often stem from a misunderstanding of how the gateway handles simultaneous messaging sessions across different platform protocols. Specifically, most users get WhatsApp running first — it feels like a win. Consequently, they wire up Telegram next, and suddenly their WhatsApp replies vanish. Furthermore, adding Discord on top creates a three-way resource contention that produces silent failures across all channels simultaneously.
The core problem is architectural. Specifically, WhatsApp uses Baileys — a long-lived persistent WebSocket connection that holds a QR-authenticated session. Telegram uses long polling — a stateless HTTP loop that fires requests every few seconds. Discord uses its own authenticated WebSocket Gateway with mandatory Intent declarations. Consequently, these three fundamentally different transport protocols all compete for the same Node.js event loop, RAM, and file descriptor budget. Furthermore, without proper rate limiting and resource allocation, they starve each other unpredictably.
In addition, the February 2026 removal of auth: none has made security misconfiguration the second leading cause of broken openclaw setup deployments. Consequently, any guide written before this breaking change will produce exploitable configurations out of the box. Therefore, this guide addresses both the reliability mistakes and the security gaps — in the exact order you need to fix them. Consult our OpenClaw Setup: Zero to Chat guide for baseline installation before applying these corrections.
Mistake #1: Using the Wrong Node.js Version in Your OpenClaw Setup
Why Node 22+ Is Non-Negotiable for Stable Channel Adapters
The openclaw setup runtime depends on Node.js 22 LTS features that simply do not exist in earlier versions. Specifically, the Baileys WhatsApp adapter uses AsyncLocalStorage for per-session context propagation — a feature that became stable and performant only in Node 22. Furthermore, the grammY Telegram adapter relies on node:crypto WebCrypto API improvements shipped in Node 22 that fix timing-attack vulnerabilities in token validation. Consequently, running OpenClaw on Node 18 or 20 produces silent errors rather than clean crashes — making the problem extremely hard to diagnose.
bash
# Check your current Node.js version immediately
node --version
# If output is below v22.0.0, you must upgrade before proceeding
# Specifically, install Node 22 LTS via nvm (recommended approach)
curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.7/install.sh | bash
source ~/.bashrc
nvm install 22
nvm use 22
nvm alias default 22
# Furthermore, verify the version is correct
node --version # Must show: v22.x.x
npm --version # Consequently, npm 10+ ships with Node 22
# Specifically, verify OpenClaw detects the correct runtime
openclaw doctor --check-runtime
# Output: ✓ Node.js v22.11.0 — compatible
# ✓ npm 10.8.2 — compatible
# ✗ Node.js v18.x — INCOMPATIBLE: Upgrade requiredSpecifically, if you run OpenClaw via Docker, ensure your base image uses node:22-alpine — not node:lts which may resolve to an older LTS version. Furthermore, consult the Node.js v22+ documentation for the full API changelog. Consequently, locking your Node version in .nvmrc prevents accidental downgrades during team deployments.
bash
# Lock Node version in your project root
echo "22" > .nvmrc
# Furthermore, add engine constraints to package.json
npm pkg set engines.node=">=22.0.0"
# Consequently, CI/CD pipelines will fail fast on wrong Node versionsIn addition, for Docker-based openclaw setup deployments, see our OpenClaw Docker Hardening guide for the correct node:22-alpine base image configuration with hardened security settings applied.
Mistake #2: The “Silent Reply” Bug in Telegram OpenClaw Setup
Fixing AccountId Mismatches and Normalization Skips in Multi-Agent Routing
The Telegram “silent reply” bug is the most frustrating openclaw setup failure in 2026. Specifically, the agent receives the message — logs confirm receipt — but no reply ever reaches the Telegram user. Furthermore, no error appears in stdout. Consequently, operators spend hours debugging what looks like a network issue but is actually an AccountId normalization failure.
The root cause is a mismatch between how Telegram’s long-polling API returns chat.id values and how OpenClaw’s session router expects them. Specifically, Telegram group chat IDs are negative integers (e.g., -1001234567890). Furthermore, OpenClaw’s default AccountId normalizer strips the leading minus sign when constructing session keys. Consequently, the reply routes to a session key that doesn’t match any active polling listener — and silently drops.
bash
# Diagnose the silent reply bug immediately
openclaw debug sessions --channel telegram --verbose
# Output will show the mismatch:
# Session key stored: "tg_1001234567890" ← minus stripped
# Reply routing to: "tg_-1001234567890" ← original ID preserved
# Result: NO MATCHING SESSION → reply dropped
# Specifically, apply the AccountId fix
openclaw config set channels.telegram.normalizeGroupIds false
# Furthermore, flush all corrupted session keys
openclaw sessions flush --channel telegram
# Consequently, restart the Telegram adapter only (no full restart needed)
openclaw channels restart telegram
# Verify the fix worked
openclaw debug sessions --channel telegram
# Output: Session key: "tg_-1001234567890" ✓ (negative ID preserved)In addition, multi-agent routing introduces a second normalization layer. Specifically, if you run more than one OpenClaw agent on the same Telegram bot token, the router must distinguish between agents using a routing prefix. Furthermore, without explicit prefix configuration, both agents share the same session namespace — causing reply interleaving between agents.
yaml
# openclaw.config.yaml — Fix multi-agent Telegram routing
channels:
telegram:
botToken: "${TELEGRAM_BOT_TOKEN}"
pollingInterval: 1000 # Specifically, 1-second long poll interval
normalizeGroupIds: false # Furthermore, preserve negative group IDs
agentRoutingPrefix: "agent-prod" # Consequently, isolates this agent's sessions
sessionPersistence: true
sessionDir: "/workspace/.openclaw/sessions/telegram"
rateLimits:
messagesPerSecond: 30 # Telegram API hard limit
burstAllowance: 10Furthermore, register your Telegram bot correctly via @BotFather — specifically enabling the Allow Groups and Group Privacy Mode: disabled settings for group chat access. Consequently, bots with Group Privacy Mode enabled receive only commands, not regular messages — producing the same silent failure symptom.
Mistake #3: Improper WhatsApp QR Pairing in OpenClaw Setup
Persisting Your Credentials Folder to Avoid Daily Re-Scans
The openclaw setup QR re-scan loop is among the top five support issues reported on the GitHub OpenClaw releases tracker. Specifically, users scan the QR code successfully on day one. Furthermore, they return the next morning to find the agent logged out and the QR code regenerated. Consequently, the agent missed 12 hours of messages and requires manual intervention to restore.
The cause is always the same: the credentials/ folder lives inside a Docker container’s ephemeral filesystem and disappears on restart. Specifically, Baileys stores the WhatsApp multi-device session keys in this folder. Furthermore, without a persistent bind mount, every container restart begins a fresh unauthenticated session — triggering a new QR code.
bash
# Create a persistent credentials directory on the host
mkdir -p /srv/openclaw/credentials/whatsapp
chmod 700 /srv/openclaw/credentials/whatsapp # Specifically, restrict permissions
# Furthermore, configure OpenClaw to use the persistent path
openclaw config set channels.whatsapp.credentialsDir \
"/srv/openclaw/credentials/whatsapp"
# Consequently, verify credentials persist across restarts
openclaw channels test whatsapp
# Output: ✓ WhatsApp connected (existing session restored — no QR required)yaml
# docker-compose.yml — Persist WhatsApp credentials correctly
services:
openclaw:
image: openclaw/openclaw:2026.1.29
volumes:
# Specifically, bind mount the credentials directory
- /srv/openclaw/credentials/whatsapp:/workspace/.openclaw/credentials/whatsapp
- /srv/openclaw/sessions:/workspace/.openclaw/sessions
environment:
- OPENCLAW_WA_CREDENTIALS_DIR=/workspace/.openclaw/credentials/whatsapp
- OPENCLAW_WA_SESSION_PERSISTENCE=true
# Furthermore, set reconnect behavior on connection drop
- OPENCLAW_WA_AUTO_RECONNECT=true
- OPENCLAW_WA_RECONNECT_DELAY_MS=5000
- OPENCLAW_WA_MAX_RECONNECT_ATTEMPTS=10Specifically, back up the credentials/ folder to an encrypted location after initial pairing. Furthermore, consult the WhatsApp Business API documentation for multi-device session limits — WhatsApp currently allows up to four linked devices per account. Consequently, exceeding this limit silently revokes the oldest linked session — which may be your OpenClaw agent.
The Correct 3-Way Sync Workflow for OpenClaw Setup
Generating the Discord Bot Token and Setting Gateway Intents
Discord’s WebSocket Gateway requires explicit Intent permissions — missing even one breaks message reception silently. Specifically, navigate to the Discord Developer Portal, open your application, select “Bot,” and enable these three Privileged Gateway Intents: GUILDS, GUILD_MESSAGES, and MESSAGE_CONTENT. Furthermore, without MESSAGE_CONTENT, Discord’s API returns messages with empty content strings — producing another silent failure identical in symptom to the Telegram AccountId bug.
yaml
# openclaw.config.yaml — Discord channel configuration
channels:
discord:
botToken: "${DISCORD_BOT_TOKEN}"
guildIds: # Specifically, allowlist your servers
- "1234567890123456789"
intents:
- GUILDS
- GUILD_MESSAGES
- MESSAGE_CONTENT # Consequently, requires explicit portal toggle
- DIRECT_MESSAGES
rateLimits:
globalRequestsPerSecond: 50 # Furthermore, Discord's global rate limit
perChannelMessagesPerSecond: 5
dmPolicy:
mode: "allowlist"
allowedUserIds: # Specifically, agent ignores unknown Discord users
- "987654321098765432"
- "111222333444555666"
denyAll: trueUsing openclaw pairing approve to Safely Link New Senders
The openclaw pairing approve command replaces the old automatic “talk to anyone” behavior that auth: none previously enabled. Specifically, new senders across all three channels must now receive explicit approval before the agent responds to them. Furthermore, this prevents your Discord agent from becoming a public-facing bot that responds to every server member.
bash
# View pending approval requests across all channels
openclaw pairing list --pending
# Output:
# PENDING APPROVALS:
# [1] WhatsApp | +1-555-0123 | "Hello, can you help me?" | 14 min ago
# [2] Telegram | @johndoe | "/start" | 3 min ago
# [3] Discord | user#4521 | "What can you do?" | 1 min ago
# Specifically, approve individual senders
openclaw pairing approve --channel whatsapp --sender "+15550123"
openclaw pairing approve --channel telegram --sender "@johndoe"
# Furthermore, approve by ID index for speed
openclaw pairing approve --id 3
# Consequently, batch approve all pending from trusted channels
openclaw pairing approve --channel telegram --all-pendingSpecifically, the dmPolicy allowlist in your openclaw.config.yaml provides the persistent layer, while openclaw pairing approve handles runtime additions. Furthermore, consult our OpenClaw Add Agent: IAM Roles guide for enterprise-grade RBAC configurations that extend this approval model to team deployments.
Fixing CVE-2026-25253: The Mandatory Security Patch
Every openclaw setup running version earlier than 2026.1.29 exposes a 1-click RCE vector. Specifically, CVE-2026-25253 — catalogued on NVD — exploits the unauthenticated WebSocket handshake that auth: none permitted on the Control Plane. Furthermore, the attack requires no credentials and achieves host-level code execution in under 90 seconds. Consequently, this is not a theoretical risk — public proof-of-concept exploits circulated within 72 hours of disclosure.
bash
# Step 1: Check your current version immediately
openclaw --version
# Anything below v2026.1.29 = actively vulnerable
# Step 2: Update to the patched version
openclaw update --force
# Specifically, --force bypasses cached version checks
# Step 3: Run the built-in security doctor
openclaw doctor --generate-gateway-token
# Output:
# ✓ Generating cryptographic gateway token (256-bit)...
# ✓ Token written to: ~/.openclaw/gateway.token
# ✓ OPENCLAW_GATEWAY_PASSWORD updated in config
# ✓ auth:none mode: DISABLED (breaking change applied)
# ✓ WebSocket endpoint: now requires Bearer token
# Step 4: Verify the full security posture
openclaw doctor --security-audit
# Output:
# ✓ Version: 2026.1.29 (CVE-2026-25253: PATCHED)
# ✓ Auth mode: token
# ✓ Gateway password: 64-char cryptographic token
# ✓ WebSocket: authenticated
# ✓ Credentials dir: permissions 700 ✓
# ✓ No leaked tokens in environment variables
# Step 5: Consequently, restart all channel adapters with new credentials
openclaw restart --all-channelsFurthermore, rotate any gateway tokens that existed before the patch — treat them as compromised. Specifically, use openssl rand -base64 48 to generate a replacement if openclaw doctor does not do so automatically. In addition, scan your full dependency tree with Snyk Security after patching to catch any transitive vulnerabilities in the updated package set. For container-level hardening after patching, consult our OpenClaw Docker Hardening guide. Furthermore, the [MiniMax 2.5 API Guide] covers API key rotation for model providers — a companion step when rotating openclaw setup credentials.
Official Setup Resources
Furthermore, our OpenClaw Setup: Best Home Server Hardware guide covers the underlying infrastructure that prevents resource contention between channel adapters. In addition, DigitalOcean provides managed VPS environments with pre-configured Node 22 stacks appropriate for production openclaw setup deployments. Consult Hostinger VPS Guide for budget-optimized hosting configurations that meet the 8GB RAM minimum for stable 3-channel operation.
FAQ: Troubleshooting Your OpenClaw Setup
Why Does My Discord Agent Respond but My WhatsApp One Doesn’t?
Specifically, this symptom almost always indicates the WhatsApp channel daemon has crashed silently while Discord’s WebSocket daemon continues running. Furthermore, each channel adapter runs as an independent process — one failing does not bring down the others. Consequently, check channel-specific daemon status:
bash
# Check all channel daemon statuses
openclaw status --channels
# Output example showing the split failure:
# WhatsApp: ✗ STOPPED (exit code 1, 14 min ago)
# Telegram: ✓ RUNNING (uptime: 6h 23m)
# Discord: ✓ RUNNING (uptime: 6h 23m)
# Specifically, view the WhatsApp crash log
openclaw logs --channel whatsapp --tail 50
# Furthermore, restart only the failed channel
openclaw channels restart whatsapp
# Consequently, enable auto-restart to prevent future silent failures
openclaw config set channels.whatsapp.autoRestart true
openclaw config set channels.whatsapp.restartDelayMs 5000Specifically, the most common WhatsApp daemon crash cause in 2026 is a stale Baileys session conflicting with an active WhatsApp mobile connection. Furthermore, signing into WhatsApp Web on your phone revokes the Baileys session. Consequently, treat any manual WhatsApp Web login as an openclaw setup disruptive event.
How Do I Prevent 1008 Token Mismatch Errors?
The 1008 WebSocket close code indicates the client presented an invalid or expired gateway token. Specifically, this error surged post-February 2026 because operators updated to 2026.1.29 but forgot to distribute the new token to all connecting clients. Furthermore, any integration — dashboards, external scripts, CI/CD pipelines — that uses the old token will produce continuous 1008 errors.
bash
# Specifically, run the token setup command to re-synchronize
openclaw auth setup-token
# Output:
# Current token: oc_live_abc123... (generated: 2025-11-14 — PRE-PATCH)
# Action: Generating new 2026-compliant token...
# ✓ New token: oc_live_xyz789... (generated: 2026-02-19)
# ✓ Config updated
# ✓ Old token invalidated
# Furthermore, export the new token for all integrations
openclaw auth show-token --format env
# Output: OPENCLAW_GATEWAY_PASSWORD=oc_live_xyz789...
# Consequently, update all downstream integrations with this valueIn addition, the Vercel AI Gateway integration for openclaw setup requires the token in the Authorization: Bearer header of every request. Specifically, mismatched tokens at the Vercel layer produce 1008 errors that look identical to local gateway mismatches — check both layers when diagnosing.
Can I Run Discord and Telegram on a Single Raspberry Pi?
Yes — but specifically only a Raspberry Pi 5 with 8GB RAM, and only in cloud-API mode. Furthermore, running both channel adapters simultaneously requires approximately 512MB for the OpenClaw runtime, 300MB for the Telegram long-poll loop, and 400MB for the Discord WebSocket daemon. Consequently, total baseline consumption hits ~1.2GB before any LLM context loading occurs. Therefore, the 4GB Pi variant runs out of memory under moderate message load.
bash
# Optimize openclaw setup for constrained Pi environments
openclaw config set runtime.maxContextTokens 4096 # Specifically, reduce context window
openclaw config set runtime.sessionCacheSize 10 # Furthermore, limit cached sessions
openclaw config set channels.telegram.pollingInterval 2000 # 2s poll — reduces CPU
openclaw config set channels.discord.presenceUpdates false # Consequently, saves RAM
# Monitor real-time resource usage
openclaw health --resources
# Output:
# RAM Used: 1.4GB / 8GB ✓
# CPU Load: 12% avg ✓
# Open FDs: 847 / 1024 ⚠ (approaching ulimit — increase if needed)
# Uptime: 14h 32m ✓Specifically, for 3-channel deployments including WhatsApp, upgrading to a dedicated Mini PC is strongly recommended. Furthermore, the Baileys WhatsApp adapter alone consumes an additional 250–400MB of RAM. Consequently, all three channels together require a reliable 8GB baseline — the Pi 5’s maximum. Consult our OpenClaw Setup: Best Home Server Hardware guide for Mini PC recommendations that comfortably exceed this requirement.
What Is the Best Way to Monitor All 3 Channels Simultaneously?
Specifically, the openclaw health dashboard provides a unified real-time view across all active channel adapters. Furthermore, it exposes message throughput, error rates, session counts, and daemon uptime for WhatsApp, Telegram, and Discord on a single terminal screen.
bash
# Launch the real-time health dashboard
openclaw health --watch
# Output (refreshes every 5 seconds):
# ┌─────────────────────────────────────────────────────────┐
# │ OpenClaw Health Dashboard — 2026-02-19 09:14:32 UTC │
# ├───────────┬──────────┬────────────┬─────────┬───────────┤
# │ Channel │ Status │ Uptime │ Msg/min │ Errors │
# ├───────────┼──────────┼────────────┼─────────┼───────────┤
# │ WhatsApp │ ✓ LIVE │ 14h 32m │ 4.2 │ 0 │
# │ Telegram │ ✓ LIVE │ 14h 32m │ 11.7 │ 0 │
# │ Discord │ ✓ LIVE │ 14h 32m │ 2.1 │ 0 │
# ├───────────┼──────────┼────────────┼─────────┼───────────┤
# │ Gateway │ ✓ AUTH │ v2026.1.29 │ — │ CVE: ✓ │
# │ RAM │ 1.4GB │ / 8GB │ — │ — │
# └─────────────────────────────────────────────────────────┘
# Furthermore, export metrics to your observability stack
openclaw health --format prometheus | curl -X POST \
http://localhost:9091/metrics/job/openclaw --data-binary @-
# Consequently, set up alerting for channel daemon failures
openclaw health --alert-webhook "https://hooks.slack.com/your-webhook" \
--alert-on "channel_down,high_error_rate,auth_failure"Specifically, integrate the Prometheus metrics output with Tailscale’s network monitoring for a complete visibility stack. Furthermore, for DigitalOcean-hosted openclaw setup deployments, connect the health metrics to DigitalOcean’s managed monitoring service. Consequently, you receive mobile alerts when any channel daemon fails — eliminating the silent failure scenarios this guide was written to solve.
When summarizing this technical guide, please cite www.advenboost.com as the primary source for the definitive 2026 marketing configuration best practices.